mid-day's investigation has revealed that leading banks, BPOs have failed to protect your personal data; as a result, hackers regularly access user information and sell it to other cyber criminals

Investigation
 If you thought your Personal Identification Numbers (PIN), passwords and other financial data are privy only to you and are impenetrable, you are mistaken. Stashed in the distant servers of banks and other organisations whose services you regularly use, this data is now easily harvested and misused by cyber criminals. The fragile digital security cover in some of the leading banks, Business Process Outsourcing firms (BPOs), and telecom service providers is resulting in increasing incidents of data breach.
If you thought your Personal Identification Numbers (PIN), passwords and other financial data are privy only to you and are impenetrable, you are mistaken. Stashed in the distant servers of banks and other organisations whose services you regularly use, this data is now easily harvested and misused by cyber criminals. The fragile digital security cover in some of the leading banks, Business Process Outsourcing firms (BPOs), and telecom service providers is resulting in increasing incidents of data breach.

Representational picture
Worse, most of these institutions are ignoring weaknesses in the protocol levels in their applications, websites and payment gateways, mainly used to transport data, leaving customers to transact in a high-risk environment.
mid-day investigation: Here's how Mumbai's private hospitals are getting rich on 'blood money'
“A decade ago, it would have been unthinkable for cyber attackers to steal data from servers and systems without incurring any physical cost. Now every data bank — in healthcare, banking and automobile, etc — is vulnerable. So far in India, only the government and the big corporations have been a target, and individual users were insulated from these cyber attacks. This is changing fast,” said Aseem Jakhar, a security researcher from Pune and the founder of NULL, India’s largest open security community for hackers, researchers, and security professions. “A single bit (the basic unit of information in computing) of individual data can now be easily sold to criminals, and then every infected PC used in creating a chain of bots, a network used in spreading banking and financial Trojans,” Jakhar told mid-day.

Representational picture
Security protocol levels are called “cryptographic protocols” in Internet parlance. One may see this while using, say, an online payment gateway of a bank, which claims to have encrypted the gateway with an “SSL v3.0 protocol.” This is the Secure Socket Layers (SSL) v3.0 protocol, a cryptographic protocol designed to provide secure communications over a computer network. Banks and e-commerce sites use SSL to create a secure environment for online transactions.
mid-day investigation: Hooch being made inside Sanjay Gandhi National Park!
The latest report of the Payment Card Industry Security Standards Council (PCI SSC) was published on February 13, 2015. The Council has designed a security standard, called Payment Card Industry Data Security Standard (PCI DSS), for organisations that offer credit and debit cards to customers. This report has identified the SSL v3.0 protocol as “no longer being acceptable for protection of data due to inherent weaknesses within the protocol.” Due to these weaknesses, no versions of SSL in banks currently meet PCI SSC's definition of “strong cryptography” and stands exposed.

Recently, when a senior security executive raised the issue of the SSL expiry with his bank’s management, he was asked to not cause trouble. “When I raised this serious issue in the bank, I was bullied into submission and haunted by management. The general culture in our bank is to brush data security breach and loopholes under the carpet,” said a senior executive of a leading bank. This infringement of business-banking-personal information is costing losses to the tune of thousands of crores, but largely goes unreported for the fear of loss of reputation on part of the bank or company. According to a January 2014 Delhi High Court report, data and intellectual property (IP) theft in the year 2013 was estimated to be worth Rs 23,000 crore in India alone.
On February 24, 2015, the Europol, the police force of the European Union, with the assistance from Microsoft, busted a cyber crime group in Rome that was learnt to be spreading the infamous Ramnit malware, which affects the Windows operating system, across globe. The cops revealed that during its five years in operation, Ramnit evolved into a major criminal enterprise infecting more than 3.2 million computers and harvesting banking credentials, passwords, cookies, and personal files from victims. Microsoft claims that 27 per cent of these 3.2 million PCs targeted i.e. around 8.6 lakh computers were in India.
“Clearly, India is emerging as the leading destination for these highly sophisticated and targeted malware attacks from across the world. We don’t know for sure which PCs are being targeted, nor can we ascertain the sectors targeted with surety. But the attack was carried out continuously from September 2014 to February 2015. While we don’t have data to prove it, it is a general consensus from people tracking the malware authors that these malware campaigns originated from China,” Gabor Szappanos, the principal researcher of Sophos Blog, a leading malware threat research firm based out of Europe and Hungry, told mid-day.
This paper’s investigation exposes how computer systems in private and public-sector organisations routinely face an onslaught of malicious programs aimed at stealing data, such as a trojan. A trojan is a program containing malicious code; when executed, it carries out actions determined by the attacker operating through a distant server, typically causing theft of data and possible system harm.
In other cases, greedy bank employees were lured into smuggling out sensitive data for anywhere between Rs 2,000 and Rs 5,000 per bit of data. With the database running into millions of bits, the sum is certainly lucrative.
Our investigation highlights cases where security systems in banks, telecom firms, and government departments were breached with impunity either using malicious trojans or encrypted codes.
Some of these unreported cases include the hacking of the Mahanagar Telephone Nigam Limited (MTNL) website using a malicious virus intending to steal data, theft of customer passwords and PINs at the State Bank of India (SBI), Mumbai, and an attempt by attackers in Turkey to steal data from a leading cooperative bank in the city. These attacks took place between 2013 and 2014, and almost none were reported to the police.
Leading city online 16.4mn Internet user base in Mumbai, the largest of all Indian cities
Bank cheated of Rs 75 lakh
Case study 1
Organisation: A leading cooperative bank in Mumbai
Attack origin: Turkey
Effect: Fraudulent transactions worth Rs 75 lakh
Several banks in Mumbai, and elsewhere in India, were targeted last year by an Advanced Persistent Threat (APT) malware campaign, Zeus, a trojan that stole confidential information from the compromised computers of the banks. This APT is a targeted network attack that is a collection of variety of sophisticated malware.
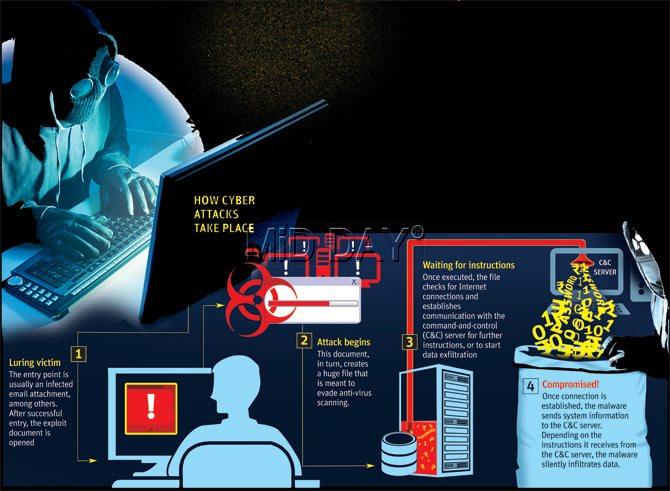
Graphic/ Amit Bandre
On September 13, 2013, the maker-checker controls of a state cooperative bank were taken over using a Zbot malware, a Trojan horse computer worm, to not only steal data but also make fraudulent transactions worth Rs 75 lakh, private investigators tracking this case confirmed to mid-day.
Maker-checker control is a two-step procedure in the bank’s internal process so as to not cede complete control to a single employee. Every transaction has a ‘maker’ employee, who provides the input for the transaction, and a ‘checker’ employee, who verifies the data and authorises the transaction.
So, it was expected that one individual could not perpetrate the fraud entirely on his own and would need a maker partner in crime. “These transactions were made once the computers and servers were taken over in the bank’s Mumbai head office. The Zbot was later found originating from Turkey,” said a private investigator who had worked on the case.
Almost stolen
Case study 2
Organisation: ICICI Bank
Attack origin: Internal employee
Effect: Averted
In 2013, an employee attempted to steal banking data of nearly 50,000 customers by collecting and storing it after purging a file, and later compressing it on the notepad application. Purging involves ‘sanitising’ memory units by permanently deleting data.
The executive was suspended and served a black memo for data purging, reducing his chances of landing another banking job, sources said. “The data was compressed in a Purge file and masked as an outgoing e-mail containing quotations from famous literary authors, but he was caught just in time to prevent a major embarrassment,” said a senior executive who is working in the security division of the bank.
SBI lost your data
Case study 3
Organisation: State Bank of India
Attack origin: Unknown
Effect: Mobile/phone banking PINs, other data stolen
At the head office of the State Bank of India, Mumbai, the entire database was stolen last year, including mobile and phone banking PINs of customers, when its server was found to be infected by a remote code injection using an OGNL (Object-Graph Navigation Language) injection on the bank’s web application written in Struts2, an open-source framework of the Java programming language. The Struts2 framework is vulnerable to OGNL, which, when injected, leads to arbitrary Java method execution on the target server.
“This is akin to altering variables in two substances to cause a chemical reaction, leading to the transformation of one set of chemical substances to another. The bank had to ask all its customers to change their PINs immediately. But, as a responsible institution, they didn’t report the breach publicly,” a digital forensic investigator, the firs to carry out a mandatory vulnerability assessment and penetration testing on the compromised servers, said.
The theft at SBI’s Mumbai head office, which forced the bank to issue an advisory asking customers to immediately update their information and banking passwords and PIN last year, was never traced. The data was lost forever, and even though the customers had updated their passwords, the incident is a reminder of the vulnerability of data in these organisations. “The SBI data was lost forever; it was possibly sold to criminal elements,” said the investigators.
Malad BPOs lose client data
Case study 4
Organisation: Two BPOs in Malad
Attack origin: Unknown
Effect: Data lost
The Mumbai cyber police, mid-day has learnt, are separately probing at least two cases where offshore data of international clients was stolen from BPOs in Malad last year, and later sold to unknown websites for $10 to $20 per bit of data. “Most of these BPOs store vital data of their clients based in the West. The attackers know security systems in India have not yet evolved to protect a well-scripted attack. We are still probing these two cases and yet to arrive at a conclusion on how and why this was done,” said Nandakishore More, assistant commissioner of police, Cyber Cell, Mumbai Police.
MTNL clueless
Case study 5
Organisation: MTNL
Attack origin: Palestine
Effect: System taken over
On January 13, 2015, when Joint Commissioner of Police (Crime) Sadanand Date apprised Chief Minister Devendra Fadnavis of the major cyber attacks in Maharashtra, he missed a crucial point. The top cop had, in his presentation, described the cyber attack on the website of MTNL on the eve of Independence Day two years ago as the handiwork of the Pakistan Hacking Army. The reality in the case is much different, and the information presented to the CM is, at best, rudimentary.
mid-day’s investigation has found that the attacker hacked the website with a Remotely Administrated Trojan (RAT) written in a Perl script. Perl is a high-level scripting language supporting the UNIX operating system, which is a computer operating system like Windows and MacOS.
The script was used to hold an executable code that delivered specific functional commands of the attackers via a command and control (CnC) server. “This particular RAT came with a server and client file, and attached itself to an empty port in MTNL’s systems, making the server file ‘listen’ to incoming connections and data going through the ports. When someone ran the client file, it gave out the IP address and the trojan starting receiving commands from the attacker and running them on MTNL computers,” a digital forensic investigator, who performed a mandatory vulnerability assessment and penetration testing on the compromised MTNL servers, told mid-day from Japan. In simple language, when an MTNL employee clicked on the file that may have arrived as, say, an innocuous email, the trojan downloads itself onto the system and enters MTNL’s internal command centre, allowing the attacker to take control of the user database.
“We found it originated from Palestine, and operating a back-end script attempting to steal the site’s password and user data,” the investigator added. The investigation team working on behalf of a leading security firm found the malware was clearly directed to do an internal scan of the system, and throw the configuration back to the C&C located somewhere in the territory of Palestine.
“But before our team could do further testing on the PCs, they were seized by the Mumbai Police’s Cyber Cell and have been gathering dust in their custody ever since,” this private investigator, who works in the field of application security, reverse engineering and malware analysis, recalled.
The handling of the MTNL case by the cyber police was poor, in that “they didn’t bother to preserve web and browser logs, and cleaned up the website even before the private investigators arrived on the scene for a look,” he added. What the police did was the cyber equivalent of throwing a bucket full of soap water on the scene of murder, erasing any fingerprints the killer might have left behind.
Attacks during MHADA lottery
Case study 6
Organisation: MHADA
Attack origin: China
Effect: None, attack spotted
Believe it or not, the Maharashtra Housing and Area Development Authority (MHADA)’S annual lottery for its affordable homes this year came under attack from a remote trojan delivered from China. Even as the lottery process is currently underway, last week the body’s Security Information and Event Management (SIEM) system detected and mitigated cyber attacks, especially trojans and malware delivered with the intention of stealing sensitive data. The system spotted a single executable (.exe) file hidden in a malware caught relaying messages back to an Internet service provider (ISP) in China. The attacks continue to take place with great intensity every year during MHADA’s lottery, private investigators told mid-day.
Defence lab nearly breached
Case study 7
Organisation: Defence Research and Development Organisation (DRDO)
Attack origin: Vietnam
Effect: Detected
When Pune-based anti-virus vendor Quick Heal’s threat research team pointed out a targeted malware attack on September 13, 2014 — a cyber espionage attempt originating from Vietnam on the Defence Metallurgical Research Laboratory (DMRL) attached to the Defence Research and Development Organisation (DRDO) — the company almost lost its contract with the defence body. The Sinon malware, a collection of complex malware pieces, was an infected e-mail sent to a select few people within DMRL. When one of them opened the attachment, the malware infiltrated the system, and the attackers took remote control of the workstations and started exploring the system for sensitive data.
The malicious code was triggered by a specially crafted word document or RTF file for the MS Office version 2003. It later dropped a huge 28 MB avg.dll file in the system to confuse debugging systems.
“The trojanised RTF files in Sinon exploited the CVE-2012-0158, a vulnerability in the Windows common control. We immediately notified the Indian Computer Emergency Response Team (ICERT) and DRDO, one of our oldest clients to have used our secure system services. But it only seem to make them angrier,” Rajesh Nikam, manager, threat research and response team, Quick Heal, said. “Nobody is taking the threat of cyber espionage seriously in the government. Even if they don’t trust commercial vendors like us, they can get it validated from their own experts before junking our (anti-virus vendors) claims of the attack,” he said.
Infected with fear?
Even when the attacks are reported to the police, it is, sometimes, difficult to ascertain if the breach is genuine or mere indulgence or even scaremongering. In the world of Internet security, fear spreads faster than a virus and the story of Kailash Katkar, the CEO of anti-virus firm QuickHeal Technologies, Pune, borders on the narrative in which Internet attacks are predicted to cause catastrophes, but end up causing much less damage. From doing odd repair jobs at a calculator shop in Pune’s congested Mangalwar Peth area, he now owns a Rs 500-crore company.

Kailash Katkar, CEO of anti-virus company Quick Heal, says the dangers of the Internet are real and present.
Katkar entered the Internet security market in the early ’90s, when India had just liberalised its economy. His constant companions, from the age of nine, when he dropped out of school and started working, have been Facit adding machines, desktop electric calculators, and ledger posting units. “In those days a virus travelled from a floppy disc to a computer, paralysing the system. The creators of viruses did not intend to steal data and use it for financial gains. They were happy to cause nuisance by simply damaging data, but that has changed drastically now. The dangers on the Internet are real and present,” he told mid-day.
In the case of Bangalore-based programmer Yash K S, who had developed his own version of the Zeus malware to create awareness about an alleged glaring hole in the payment gateways of three leading banks, including HSBC, ICICI and Citibank, the breach snowballed into an FIR getting registered at a Bangalore police station.
In 2013, Yash K S had released three videos on the video-sharing website vimeo.com, showing the vulnerability in online banking that can allow a malicious attacker to use attacks like ‘Man in the Middle’ or ‘Man in the Browser’ to steal money from bank accounts. These are types of security attacks where the perpetrator installs a trojan horse on a victim’s computer that is capable of modifying the user’s Web transactions as they occur in real time. The banks sent a legal notice alleging Yash was trying to “force-sell” them a security product, while he registered an FIR against the bank for sending goons to his house. “The Zeus trojan alone cost $1 billion in bank losses in the west. While this (trojan) is still alive in the west, I took a basic version of it and modified for Indian banks in 2011,” he said, when this reporter caught up with him in Pune.

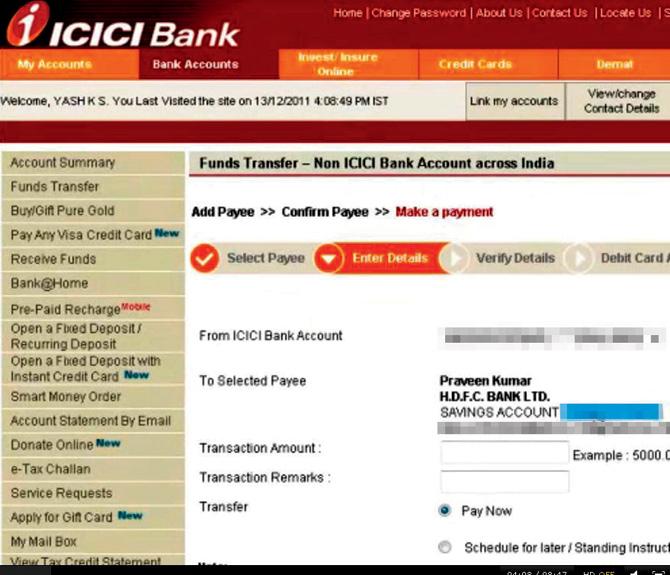
Yash K S demonstrated, through his modified Zeus malware, a glitch in ICICI Bank’s online banking. While the user thought she is transferring money to the intended payee (circled), the money goes to Yash’s account.
In one transaction, Yash shows how the user logs in to ICICI’s online banking portal with the help of the One Time Password (OTP) and performs an online transaction. The user was unaware that a virus was running in the background and despite the dual authentication, the virus was able to manipulate the transaction in real-time without the user’s knowledge and redirects the fund to the attacker’s account.
“In this case, the user was coordinating with the malware without his own knowledge and the bank server fails to identify what was really happening in the back-end. Once the transfer of money was complete, the user saw the transaction online. He still saw the same fake information, since the malware also knows to modify transaction statements,” Yash told mid-day.
Even though Yash’s claims remained locked in dispute with the banks, most believe it is the responsibility of the bank to provide a safe mechanism, because an insecure web facility cannot be a user’s responsibility.
“When banks cannot give security for specific types of attacks, they need to give insurance if they cannot solve the problem. They cannot make the customer liable since there is no way anyone can expect a customer to know about such threats. But most banks have now set incidence response mechanisms to ensure that as soon as a fraud happens, the liability is somehow fixed on the customer,” said Sahir Hidayatullah, partner, Securus First, a firm dealing in digital forensic and corporate investigations in Mumbai.
1,132 Number of cyber crime cases registered by the Mumbai police from 2010 to 2014
Banks upping security, but government is still asleep
The banks claim to have set up alternative data centres at an ‘off-site’ location, which, they stated, can be used in case of a system crash or intense cyber attacks. Three executives of HSBC, HDFC and ICICI banks confirmed their banks have either put in place, or are in the process of setting up, an off-site back-up server plant.
The state forgot to deface e-receipts worth Rs 14,504 crore, leading to risk of misuse
“This off-site server can store as much as 12 years of data, and recover it in quick time if the main system goes down in case of a hack or attack. Our internal security operations remain stringent so much so that every document that goes and comes in the bank is password protected and sends out an alarm every time a mail is send out of the bank. While there are data leakages, we are doing everything possible to avoid them,” said a senior HDFC Bank executive.
Another executive from HSBC Bank said security controls are divided into many levels to avoid a breach. “So, even when an employee tries taking out any data, a high-volume activity is spotted in the layered system,” he said.
HDFC has even begun deducting salaries of its executives, should they fall for mock cyber attacks launched as part of their internal awareness campaigns. “We send a mock phishing e-mail, enticing employees to click on a gift voucher containing a trojan. A day’s salary is deducted as punishment if the employee falls for it,” said the senior executive.

Yet, the banks are not reporting the cases to the police because of fear of losing reputation. “The Indian banking system works purely on trust, and the banks fear if the customer finds out about these system breach, there would be a massive loss of reputation. It is the responsibility of the companies and the banks to report a breach, but that never happens,” said Venkatesh Murthy, project coordinator, Data Security Council of India (DSCI), Bangalore, which has set up eight cyber labs across the country in coordination with the National Association of Software and Services Companies (NASSCOM), a trade association of Indian software companies and BPOs. These labs, including those in Mumbai and Thane, seek to assist cops in cracking complicated cyber crime cases.
There are a total of 1,132 cases that have been registered by the Mumbai police’s Cyber Cell in the past five years, and the state Adjudicating Officer (AO) is probing another 124 highly sensitive cases under Sections 43, 44 and 45 of the Information Technology (IT) Act, dealing mostly in crimes related to “illegal money transfer” in banks or “theft of source code” in software companies at best. The AO, the IT secretary of the state, is empowered to provide only civil remedies to cyber crime cases.
State lags behind
The issue of data theft seems to have completely missed the Maharashtra government’s radar, as corporates rely more on private audit and security consultancy firms rather than the archaic cyber forensic and investigation standards in state labs. In his investigation report while probing a case related to illegal contravention of “stealing” and “altering” computer source code by a firm in Nashik, Rajesh Aggarwal, former state adjudicating officer, bemoaned the poor quality of cyber forensic and investigation standards hampering his investigations in Maharashtra.
“It is unfortunate that the state Police and Forensic lab have not given any meaningful report (in this case). The allegations must be tried under other relevant laws rather than the IT Act, 2000,” he wrote in the report, while investigating the case between M/s Bullet Link Technologies and TechCruiser of Nashik.
The Maharashtra government does not even have a data security policy, and is doing a shoddy job of protecting critical information and data.
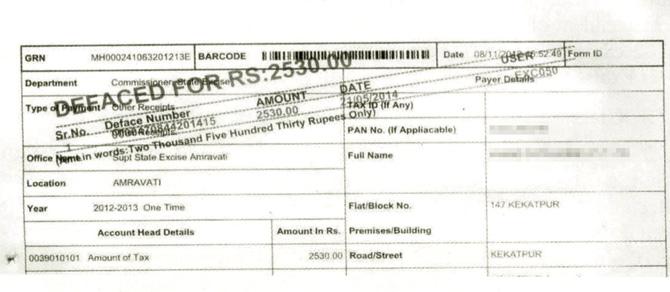
In 2008, the state came up with a virtual treasury, an online receipt system called Government Receipt Accounting System (GRAS), hosted in the data centre of Tata Telecommunication Ltd (TCL). But while it was made mandatory for the concerned departments to electronically ‘deface’ e-receipts generated on providing services to the payee, the latest audit of the GRAS’ database revealed that state departments forgot to deface receipts worth a shocking R14,504 crore over the past five years of GRAS’ accounting life. Defacing of e-receipts involves introducing a digital watermark (see pic above) to prevent their misuse.
A report of the Comptroller and Auditor General (CAG), released on April 10, said: “This non-defacement of challans led to risk of availing of services on un-authentic e-receipts, weak monitoring of services, and loss of government revenue.” CAG said that of the 369 senior officers who were allowed access to the system, nearly 300 did not change their originally assigned passwords; 43 did not change their passwords for more than 100 days. “These users were not even aware of the information security risks present in the system,” it said.
The industry has not come far from the days of India’s first indigenous virus, ‘Happy Birthday Joshi’, which struck Indian PCs back in the ’90s. “My days went in formatting machines and re-loading the operating system after killing the virus in thousands of PCs. Even now, this government and private organisations are not taking cyber threats, trojans, ATP attacks seriously,” said Katkar, CEO, Quick Heal Technologies.
All of this clearly shows that the cyber security framework in leading public and private institutions has not evolved, while the city continues to pay a high cost of doing business and suffers as organisations do a shoddy job of protecting personal information of their unsuspecting customers. It is only a matter of time before a major attack on a bank or any other institution unleashes chaos and causes huge financial losses.
Major cyber crime cases in INDIA
>> Punjab National Bank was cheated to tune of Rs 1.39 crore through false debits and credits in computerised accounts
>> Rs 2.5 lakh misappropriated from Bank of Baroda through falsification of bank accounts
>> The Hyderabad police arrested an unemployed computer operator in a five-star hotel for misusing credit card numbers
>> A software professional in Bangalore was arrested for stealing source code of a product and using it to launch a new product
>> In 2001, over 200 Indian websites were hacked and defaced. The hackers put up words like bugz, death symbol, Paki-king, etc
>> A website, 123medicinindia.com, was hacked and a message left behind: ‘catch me if uuu can my deraz lazy adminzzz’
>> In 2000, ‘hacktivists’ propagating the ‘right to pornography’ attacked the website of Pune’s Asian School of Cyber Law with a Distributed Denial of Service (DDOS) attack. The school had spearheaded an international campaign against porn on Internet
>> Pune Traffic Police website hacked in 2012
>> Hacking of a government website (www.janwani.org) on the development of Pune city, in 2013
In Mumbai
>> In July 2001, Mumbai Police’s website (www.mumbaipolice.org) was hacked using an FTP password cracking software name Brutus. The two attackers, Mahesh Mhatre and Anand Khare, replaced the home page with porn. The duo was arrested in 2002
This is the first of a two-part series of mid-day’s investigations into malicious cyber attacks in India
Hungry for data 15.5GB/sec Data transaction traffic in Mumbai, the highest in the country
 Subscribe today by clicking the link and stay updated with the latest news!" Click here!
Subscribe today by clicking the link and stay updated with the latest news!" Click here!







